OT-IACS Cybersecurity Training
Introduction and awareness training

OT-IACS Cybersecurity introduction - Awareness Training
เรียบเรียง ตาม Framework
อ้างอิง ข้อ แนะนำการนำไปประยุกติ์ จาก
and also knowledge sharing and discussion from a decade of experience in Control system implementation
OT-Industrial Cyber security Awareness Training
Raise awareness for your IT/ OT-ICS personal of current industrial Cybersecurity, differences and similarities, general Cybersecurity basics and industrial Cybersecurity specifics.
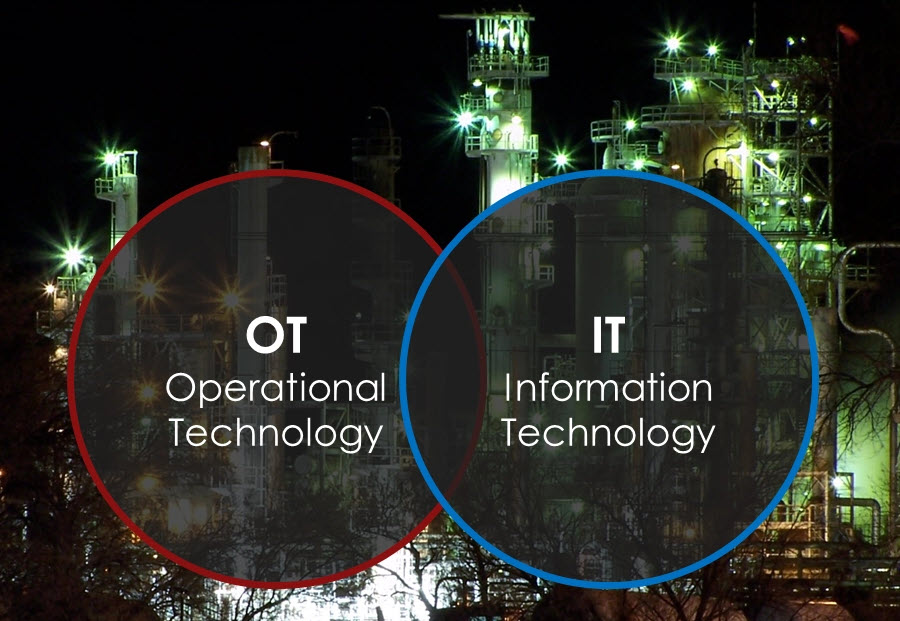
Personal will learn to clarify the key differences between typical OT-ICS and pure IT network, and understand the evolution in OT-ICS Cybersecurity.
Course Goal:
- Understand OT-ICS Network basics: typical topology, components, protocols
- Understand Information security basics: attack vectors, threats, vulnerabilities, etc.
- Know principle to Identify countermeasures: segmentation and etc.
- Getting to know standard and recommendations
Course Contents:
-
ICS Cybersecurity Landscape
- Recognize Cybersecurity in your overall risk management process.
- Identify types of ICS threats, vulnerabilities, and consequences.
-
Difference between IT and ICS
- Network basics: the architecture and topology of IT and ICS
- Common ICS component
- Identify ICS type
- Discuss Data flow within ICS
- Recognize ICS communication typologies and methods
-
Attack Methodologies in IT & ICS
- Describe the anatomy of a Cyber attack.
- Recognize how attack methods can apply to control systems.
-
Countermeasures
- Standard and Practice
Introduction to ISA/IEC 62443 – Standard and aspect of NIST SP 800 - 82
Getting to know a structural concept, approach and methodology when consider managing ICS Cybersecurity
Course Goal:
- Discuss the need and importance for control system security
- Learn about current principles and best practices
- Understand the structure and content of the ISA/IEC 62443 series of documents and NIST SP 800 - 82 framework
- Discuss the principles behind the creating of an effective long term program security
- Learn the basics of risk analysis, industrial networking and network security
- Understand the concepts of defense in depth and zones and conduits
- Learn how to apply key risk mitigation techniques in principle
- Visit the recommendation and key takeaway from NIST SP800 - 82
Course Contents:
-
Control System cybersecurity – by definition
- Trend and potential impact
-
Reference standard – ISA/IEC62443 and NIST SP 800 - 82 Framework
- Structure, Phase, Role, responsibility discussion
- Approach and development of NIST SP 800 - 82
-
Concept used in ISA/IEC62443 and NIST SP 800 - 82
- Defense-in Depth
- Zones and Conduits
- Model
- Steps and instructions recommended by NIST Framework
-
Cybersecurity requirements, assumptions and constraints
- Need to address security
-
Applying ISA IEC62443 in control system and what NIST SP 800 - 82 has recommended
-
Security Risk Assessment and System Design
- Security Levels (SL)
- Foundational Requirements (FR)
-
Establishing an Industrial Automation and Control Systems Security Program
- Process to Develop a CSMS
-
Cybersecurity Life Cycle for IACS
Contact
email: nuttapong@koennen.co.th; Tel. 66 62 3944987, 66 81 9062927
